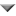CWE VIEW: Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors
CWE entries in this view (graph) are listed in the 2010 CWE/SANS Top 25 Programming Errors. This view is considered obsolete as a newer version of the Top 25 is available.
The following graph shows the tree-like relationships between
weaknesses that exist at different levels of abstraction. At the highest level, categories
and pillars exist to group weaknesses. Categories (which are not technically weaknesses) are
special CWE entries used to group weaknesses that share a common characteristic. Pillars are
weaknesses that are described in the most abstract fashion. Below these top-level entries
are weaknesses are varying levels of abstraction. Classes are still very abstract, typically
independent of any specific language or technology. Base level weaknesses are used to
present a more specific type of weakness. A variant is a weakness that is described at a
very low level of detail, typically limited to a specific language or technology. A chain is
a set of weaknesses that must be reachable consecutively in order to produce an exploitable
vulnerability. While a composite is a set of weaknesses that must all be present
simultaneously in order to produce an exploitable vulnerability.
Show Details:
800 - Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp)
Weaknesses in this category are not part of the general Top 25, but they were part of the original nominee list from which the Top 25 was drawn.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
134
(Use of Externally-Controlled Format String)
The product uses a function that accepts a format string as an argument, but the format string originates from an external source.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
212
(Improper Removal of Sensitive Information Before Storage or Transfer)
The product stores, transfers, or shares a resource that contains sensitive information, but it does not properly remove that information before the product makes the resource available to unauthorized actors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
307
(Improper Restriction of Excessive Authentication Attempts)
The product does not implement sufficient measures to prevent multiple failed authentication attempts within a short time frame.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
330
(Use of Insufficiently Random Values)
The product uses insufficiently random numbers or values in a security context that depends on unpredictable numbers.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
416
(Use After Free)
The product reuses or references memory after it has been freed. At some point afterward, the memory may be allocated again and saved in another pointer, while the original pointer references a location somewhere within the new allocation. Any operations using the original pointer are no longer valid because the memory "belongs" to the code that operates on the new pointer.
Dangling pointer
UAF
Use-After-Free

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
426
(Untrusted Search Path)
The product searches for critical resources using an externally-supplied search path that can point to resources that are not under the product's direct control.
Untrusted Path

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
454
(External Initialization of Trusted Variables or Data Stores)
The product initializes critical internal variables or data stores using inputs that can be modified by untrusted actors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
456
(Missing Initialization of a Variable)
The product does not initialize critical variables, which causes the execution environment to use unexpected values.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
476
(NULL Pointer Dereference)
The product dereferences a pointer that it expects to be valid but is NULL.
NPD
null deref
NPE
nil pointer dereference

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
59
(Improper Link Resolution Before File Access ('Link Following'))
The product attempts to access a file based on the filename, but it does not properly prevent that filename from identifying a link or shortcut that resolves to an unintended resource.
insecure temporary file
Zip Slip

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
672
(Operation on a Resource after Expiration or Release)
The product uses, accesses, or otherwise operates on a resource after that resource has been expired, released, or revoked.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
681
(Incorrect Conversion between Numeric Types)
When converting from one data type to another, such as long to integer, data can be omitted or translated in a way that produces unexpected values. If the resulting values are used in a sensitive context, then dangerous behaviors may occur.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
749
(Exposed Dangerous Method or Function)
The product provides an Applications Programming Interface (API) or similar interface for interaction with external actors, but the interface includes a dangerous method or function that is not properly restricted.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
772
(Missing Release of Resource after Effective Lifetime)
The product does not release a resource after its effective lifetime has ended, i.e., after the resource is no longer needed.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
799
(Improper Control of Interaction Frequency)
The product does not properly limit the number or frequency of interactions that it has with an actor, such as the number of incoming requests.
Insufficient anti-automation
Brute force

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
808
(2010 Top 25 - Weaknesses On the Cusp) >
804
(Guessable CAPTCHA)
The product uses a CAPTCHA challenge, but the challenge can be guessed or automatically recognized by a non-human actor.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses)
Weaknesses in this category are listed in the "Porous Defenses" section of the 2010 CWE/SANS Top 25 Programming Errors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
285
(Improper Authorization)
The product does not perform or incorrectly performs an authorization check when an actor attempts to access a resource or perform an action.
AuthZ

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
306
(Missing Authentication for Critical Function)
The product does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
311
(Missing Encryption of Sensitive Data)
The product does not encrypt sensitive or critical information before storage or transmission.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
327
(Use of a Broken or Risky Cryptographic Algorithm)
The product uses a broken or risky cryptographic algorithm or protocol.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
732
(Incorrect Permission Assignment for Critical Resource)
The product specifies permissions for a security-critical resource in a way that allows that resource to be read or modified by unintended actors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
798
(Use of Hard-coded Credentials)
The product contains hard-coded credentials, such as a password or cryptographic key.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
803
(2010 Top 25 - Porous Defenses) >
807
(Reliance on Untrusted Inputs in a Security Decision)
The product uses a protection mechanism that relies on the existence or values of an input, but the input can be modified by an untrusted actor in a way that bypasses the protection mechanism.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management)
Weaknesses in this category are listed in the "Risky Resource Management" section of the 2010 CWE/SANS Top 25 Programming Errors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
120
(Buffer Copy without Checking Size of Input ('Classic Buffer Overflow'))
The product copies an input buffer to an output buffer without verifying that the size of the input buffer is less than the size of the output buffer, leading to a buffer overflow.
Classic Buffer Overflow
Unbounded Transfer

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
129
(Improper Validation of Array Index)
The product uses untrusted input when calculating or using an array index, but the product does not validate or incorrectly validates the index to ensure the index references a valid position within the array.
out-of-bounds array index
index-out-of-range
array index underflow

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
131
(Incorrect Calculation of Buffer Size)
The product does not correctly calculate the size to be used when allocating a buffer, which could lead to a buffer overflow.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
190
(Integer Overflow or Wraparound)
The product performs a calculation that can
produce an integer overflow or wraparound when the logic
assumes that the resulting value will always be larger than
the original value. This occurs when an integer value is
incremented to a value that is too large to store in the
associated representation. When this occurs, the value may
become a very small or negative number.
Overflow
Wraparound
wrap, wrap-around, wrap around

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
22
(Improper Limitation of a Pathname to a Restricted Directory ('Path Traversal'))
The product uses external input to construct a pathname that is intended to identify a file or directory that is located underneath a restricted parent directory, but the product does not properly neutralize special elements within the pathname that can cause the pathname to resolve to a location that is outside of the restricted directory.
Directory traversal
Path traversal

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
494
(Download of Code Without Integrity Check)
The product downloads source code or an executable from a remote location and executes the code without sufficiently verifying the origin and integrity of the code.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
754
(Improper Check for Unusual or Exceptional Conditions)
The product does not check or incorrectly checks for unusual or exceptional conditions that are not expected to occur frequently during day to day operation of the product.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
770
(Allocation of Resources Without Limits or Throttling)
The product allocates a reusable resource or group of resources on behalf of an actor without imposing any restrictions on the size or number of resources that can be allocated, in violation of the intended security policy for that actor.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
805
(Buffer Access with Incorrect Length Value)
The product uses a sequential operation to read or write a buffer, but it uses an incorrect length value that causes it to access memory that is outside of the bounds of the buffer.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
802
(2010 Top 25 - Risky Resource Management) >
98
(Improper Control of Filename for Include/Require Statement in PHP Program ('PHP Remote File Inclusion'))
The PHP application receives input from an upstream component, but it does not restrict or incorrectly restricts the input before its usage in "require," "include," or similar functions.
Remote file include
RFI
Local file inclusion

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components)
Weaknesses in this category are listed in the "Insecure Interaction Between Components" section of the 2010 CWE/SANS Top 25 Programming Errors.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
209
(Generation of Error Message Containing Sensitive Information)
The product generates an error message that includes sensitive information about its environment, users, or associated data.

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
352
(Cross-Site Request Forgery (CSRF))
The web application does not, or can not, sufficiently verify whether a well-formed, valid, consistent request was intentionally provided by the user who submitted the request.
Session Riding
Cross Site Reference Forgery
XSRF

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
362
(Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition'))
The product contains a concurrent code sequence that requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence operating concurrently.
Race Condition

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
434
(Unrestricted Upload of File with Dangerous Type)
The product allows the upload or transfer of dangerous file types that are automatically processed within its environment.
Unrestricted File Upload

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
601
(URL Redirection to Untrusted Site ('Open Redirect'))
The web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a redirect.
Open Redirect
Cross-site Redirect
Cross-domain Redirect
Unvalidated Redirect

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
78
(Improper Neutralization of Special Elements used in an OS Command ('OS Command Injection'))
The product constructs all or part of an OS command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended OS command when it is sent to a downstream component.
Shell injection
Shell metacharacters
OS Command Injection

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
79
(Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting'))
The product does not neutralize or incorrectly neutralizes user-controllable input before it is placed in output that is used as a web page that is served to other users.
XSS
HTML Injection
CSS

800
(Weaknesses in the 2010 CWE/SANS Top 25 Most Dangerous Programming Errors) >
801
(2010 Top 25 - Insecure Interaction Between Components) >
89
(Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection'))
The product constructs all or part of an SQL command using externally-influenced input from an upstream component, but it does not neutralize or incorrectly neutralizes special elements that could modify the intended SQL command when it is sent to a downstream component. Without sufficient removal or quoting of SQL syntax in user-controllable inputs, the generated SQL query can cause those inputs to be interpreted as SQL instead of ordinary user data.
SQL injection
SQLi
More information is available — Please edit the custom filter or select a different filter. |
|
Use of the Common Weakness Enumeration (CWE™) and the associated references from this website are subject to the Terms of Use. CWE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) and managed by the Homeland Security Systems Engineering and Development Institute (HSSEDI) which is operated by The MITRE Corporation (MITRE). Copyright © 2006–2024, The MITRE Corporation. CWE, CWSS, CWRAF, and the CWE logo are trademarks of The MITRE Corporation. |
||