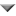CWE VIEW: Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS
CWE entries in this view (graph) are associated with the Categories of Security Vulnerabilities in ICS, as published by the Securing Energy Infrastructure Executive Task Force (SEI ETF) in March 2022. Weaknesses and categories in this view are focused on issues that affect ICS (Industrial Control Systems) but have not been traditionally covered by CWE in the past due to its earlier emphasis on enterprise IT software. Note: weaknesses in this view are based on "Nearest IT Neighbor" recommendations and other suggestions by the CWE team. These relationships are likely to change in future CWE versions.
The following graph shows the tree-like relationships between
weaknesses that exist at different levels of abstraction. At the highest level, categories
and pillars exist to group weaknesses. Categories (which are not technically weaknesses) are
special CWE entries used to group weaknesses that share a common characteristic. Pillars are
weaknesses that are described in the most abstract fashion. Below these top-level entries
are weaknesses are varying levels of abstraction. Classes are still very abstract, typically
independent of any specific language or technology. Base level weaknesses are used to
present a more specific type of weakness. A variant is a weakness that is described at a
very low level of detail, typically limited to a specific language or technology. A chain is
a set of weaknesses that must be reachable consecutively in order to produce an exploitable
vulnerability. While a composite is a set of weaknesses that must all be present
simultaneously in order to produce an exploitable vulnerability.
Show Details:
1358 - Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications)
Weaknesses in this category are related to the "ICS Communications" super category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures)
Weaknesses in this category are related to the "Zone Boundary Failures" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Within an ICS system, for traffic that crosses through network zone boundaries, vulnerabilities arise when those boundaries were designed for safety or other purposes but are being repurposed for security." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
212
(Improper Removal of Sensitive Information Before Storage or Transfer)
The product stores, transfers, or shares a resource that contains sensitive information, but it does not properly remove that information before the product makes the resource available to unauthorized actors.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
268
(Privilege Chaining)
Two distinct privileges, roles, capabilities, or rights can be combined in a way that allows an entity to perform unsafe actions that would not be allowed without that combination.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
269
(Improper Privilege Management)
The product does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
287
(Improper Authentication)
When an actor claims to have a given identity, the product does not prove or insufficiently proves that the claim is correct.
authentification
AuthN
AuthC

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
288
(Authentication Bypass Using an Alternate Path or Channel)
The product requires authentication, but the product has an alternate path or channel that does not require authentication.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
306
(Missing Authentication for Critical Function)
The product does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
362
(Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition'))
The product contains a concurrent code sequence that requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence operating concurrently.
Race Condition

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
384
(Session Fixation)
Authenticating a user, or otherwise establishing a new user session, without invalidating any existing session identifier gives an attacker the opportunity to steal authenticated sessions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
434
(Unrestricted Upload of File with Dangerous Type)
The product allows the upload or transfer of dangerous file types that are automatically processed within its environment.
Unrestricted File Upload

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
494
(Download of Code Without Integrity Check)
The product downloads source code or an executable from a remote location and executes the code without sufficiently verifying the origin and integrity of the code.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
501
(Trust Boundary Violation)
The product mixes trusted and untrusted data in the same data structure or structured message.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
668
(Exposure of Resource to Wrong Sphere)
The product exposes a resource to the wrong control sphere, providing unintended actors with inappropriate access to the resource.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
669
(Incorrect Resource Transfer Between Spheres)
The product does not properly transfer a resource/behavior to another sphere, or improperly imports a resource/behavior from another sphere, in a manner that provides unintended control over that resource.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
754
(Improper Check for Unusual or Exceptional Conditions)
The product does not check or incorrectly checks for unusual or exceptional conditions that are not expected to occur frequently during day to day operation of the product.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
829
(Inclusion of Functionality from Untrusted Control Sphere)
The product imports, requires, or includes executable functionality (such as a library) from a source that is outside of the intended control sphere.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
1189
(Improper Isolation of Shared Resources on System-on-a-Chip (SoC))
The System-On-a-Chip (SoC) does not properly isolate shared resources between trusted and untrusted agents.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
1263
(Improper Physical Access Control)
The product is designed with access restricted to certain information, but it does not sufficiently protect against an unauthorized actor with physical access to these areas.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
1303
(Non-Transparent Sharing of Microarchitectural Resources)
Hardware structures shared across execution contexts (e.g., caches and branch predictors) can violate the expected architecture isolation between contexts.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1364
(ICS Communications: Zone Boundary Failures) >
1393
(Use of Default Password)
The product uses default passwords for potentially critical functionality.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability)
Weaknesses in this category are related to the "Unreliability" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Vulnerabilities arise in reaction to disruptions in the physical layer (e.g. creating electrical noise) used to carry the traffic." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
121
(Stack-based Buffer Overflow)
A stack-based buffer overflow condition is a condition where the buffer being overwritten is allocated on the stack (i.e., is a local variable or, rarely, a parameter to a function).
Stack Overflow

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
269
(Improper Privilege Management)
The product does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
306
(Missing Authentication for Critical Function)
The product does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
349
(Acceptance of Extraneous Untrusted Data With Trusted Data)
The product, when processing trusted data, accepts any untrusted data that is also included with the trusted data, treating the untrusted data as if it were trusted.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
362
(Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition'))
The product contains a concurrent code sequence that requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence operating concurrently.
Race Condition

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
807
(Reliance on Untrusted Inputs in a Security Decision)
The product uses a protection mechanism that relies on the existence or values of an input, but the input can be modified by an untrusted actor in a way that bypasses the protection mechanism.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
1247
(Improper Protection Against Voltage and Clock Glitches)
The device does not contain or contains incorrectly implemented circuitry or sensors to detect and mitigate voltage and clock glitches and protect sensitive information or software contained on the device.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
1261
(Improper Handling of Single Event Upsets)
The hardware logic does not effectively handle when single-event upsets (SEUs) occur.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
1332
(Improper Handling of Faults that Lead to Instruction Skips)
The device is missing or incorrectly implements circuitry or sensors that detect and mitigate the skipping of security-critical CPU instructions when they occur.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
1351
(Improper Handling of Hardware Behavior in Exceptionally Cold Environments)
A hardware device, or the firmware running on it, is
missing or has incorrect protection features to maintain
goals of security primitives when the device is cooled below
standard operating temperatures.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1365
(ICS Communications: Unreliability) >
1384
(Improper Handling of Physical or Environmental Conditions)
The product does not properly handle unexpected physical or environmental conditions that occur naturally or are artificially induced.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols)
Weaknesses in this category are related to the "Frail Security in Protocols" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Vulnerabilities arise as a result of mis-implementation or incomplete implementation of security in ICS implementations of communication protocols." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
121
(Stack-based Buffer Overflow)
A stack-based buffer overflow condition is a condition where the buffer being overwritten is allocated on the stack (i.e., is a local variable or, rarely, a parameter to a function).
Stack Overflow

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
125
(Out-of-bounds Read)
The product reads data past the end, or before the beginning, of the intended buffer.
OOB read

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
268
(Privilege Chaining)
Two distinct privileges, roles, capabilities, or rights can be combined in a way that allows an entity to perform unsafe actions that would not be allowed without that combination.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
269
(Improper Privilege Management)
The product does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
276
(Incorrect Default Permissions)
During installation, installed file permissions are set to allow anyone to modify those files.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
290
(Authentication Bypass by Spoofing)
This attack-focused weakness is caused by incorrectly implemented authentication schemes that are subject to spoofing attacks.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
306
(Missing Authentication for Critical Function)
The product does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
311
(Missing Encryption of Sensitive Data)
The product does not encrypt sensitive or critical information before storage or transmission.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
312
(Cleartext Storage of Sensitive Information)
The product stores sensitive information in cleartext within a resource that might be accessible to another control sphere.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
319
(Cleartext Transmission of Sensitive Information)
The product transmits sensitive or security-critical data in cleartext in a communication channel that can be sniffed by unauthorized actors.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
325
(Missing Cryptographic Step)
The product does not implement a required step in a cryptographic algorithm, resulting in weaker encryption than advertised by the algorithm.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
327
(Use of a Broken or Risky Cryptographic Algorithm)
The product uses a broken or risky cryptographic algorithm or protocol.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
330
(Use of Insufficiently Random Values)
The product uses insufficiently random numbers or values in a security context that depends on unpredictable numbers.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
336
(Same Seed in Pseudo-Random Number Generator (PRNG))
A Pseudo-Random Number Generator (PRNG) uses the same seed each time the product is initialized.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
337
(Predictable Seed in Pseudo-Random Number Generator (PRNG))
A Pseudo-Random Number Generator (PRNG) is initialized from a predictable seed, such as the process ID or system time.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
341
(Predictable from Observable State)
A number or object is predictable based on observations that the attacker can make about the state of the system or network, such as time, process ID, etc.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
349
(Acceptance of Extraneous Untrusted Data With Trusted Data)
The product, when processing trusted data, accepts any untrusted data that is also included with the trusted data, treating the untrusted data as if it were trusted.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
358
(Improperly Implemented Security Check for Standard)
The product does not implement or incorrectly implements one or more security-relevant checks as specified by the design of a standardized algorithm, protocol, or technique.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
362
(Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition'))
The product contains a concurrent code sequence that requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence operating concurrently.
Race Condition

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
377
(Insecure Temporary File)
Creating and using insecure temporary files can leave application and system data vulnerable to attack.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
384
(Session Fixation)
Authenticating a user, or otherwise establishing a new user session, without invalidating any existing session identifier gives an attacker the opportunity to steal authenticated sessions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
648
(Incorrect Use of Privileged APIs)
The product does not conform to the API requirements for a function call that requires extra privileges. This could allow attackers to gain privileges by causing the function to be called incorrectly.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
787
(Out-of-bounds Write)
The product writes data past the end, or before the beginning, of the intended buffer.
Memory Corruption

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
1189
(Improper Isolation of Shared Resources on System-on-a-Chip (SoC))
The System-On-a-Chip (SoC) does not properly isolate shared resources between trusted and untrusted agents.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
1303
(Non-Transparent Sharing of Microarchitectural Resources)
Hardware structures shared across execution contexts (e.g., caches and branch predictors) can violate the expected architecture isolation between contexts.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1359
(ICS Communications) >
1366
(ICS Communications: Frail Security in Protocols) >
1393
(Use of Default Password)
The product uses default passwords for potentially critical functionality.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture))
Weaknesses in this category are related to the "ICS Dependencies (& Architecture)" super category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1367
(ICS Dependencies (& Architecture): External Physical Systems)
Weaknesses in this category are related to the "External Physical Systems" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Due to the highly interconnected technologies in use, an external dependency on another physical system could cause an availability interruption for the protected system." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1367
(ICS Dependencies (& Architecture): External Physical Systems) >
1247
(Improper Protection Against Voltage and Clock Glitches)
The device does not contain or contains incorrectly implemented circuitry or sensors to detect and mitigate voltage and clock glitches and protect sensitive information or software contained on the device.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1367
(ICS Dependencies (& Architecture): External Physical Systems) >
1338
(Improper Protections Against Hardware Overheating)
A hardware device is missing or has inadequate protection features to prevent overheating.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1367
(ICS Dependencies (& Architecture): External Physical Systems) >
1357
(Reliance on Insufficiently Trustworthy Component)
The product is built from multiple separate components, but it uses a component that is not sufficiently trusted to meet expectations for security, reliability, updateability, and maintainability.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1367
(ICS Dependencies (& Architecture): External Physical Systems) >
1384
(Improper Handling of Physical or Environmental Conditions)
The product does not properly handle unexpected physical or environmental conditions that occur naturally or are artificially induced.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems)
Weaknesses in this category are related to the "External Digital Systems" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Due to the highly interconnected technologies in use, an external dependency on another digital system could cause a confidentiality, integrity, or availability incident for the protected system." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
15
(External Control of System or Configuration Setting)
One or more system settings or configuration elements can be externally controlled by a user.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
287
(Improper Authentication)
When an actor claims to have a given identity, the product does not prove or insufficiently proves that the claim is correct.
authentification
AuthN
AuthC

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
306
(Missing Authentication for Critical Function)
The product does not perform any authentication for functionality that requires a provable user identity or consumes a significant amount of resources.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
308
(Use of Single-factor Authentication)
The use of single-factor authentication can lead to unnecessary risk of compromise when compared with the benefits of a dual-factor authentication scheme.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
312
(Cleartext Storage of Sensitive Information)
The product stores sensitive information in cleartext within a resource that might be accessible to another control sphere.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
440
(Expected Behavior Violation)
A feature, API, or function does not perform according to its specification.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
470
(Use of Externally-Controlled Input to Select Classes or Code ('Unsafe Reflection'))
The product uses external input with reflection to select which classes or code to use, but it does not sufficiently prevent the input from selecting improper classes or code.
Reflection Injection

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
603
(Use of Client-Side Authentication)
A client/server product performs authentication within client code but not in server code, allowing server-side authentication to be bypassed via a modified client that omits the authentication check.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
610
(Externally Controlled Reference to a Resource in Another Sphere)
The product uses an externally controlled name or reference that resolves to a resource that is outside of the intended control sphere.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
638
(Not Using Complete Mediation)
The product does not perform access checks on a resource every time the resource is accessed by an entity, which can create resultant weaknesses if that entity's rights or privileges change over time.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1059
(Insufficient Technical Documentation)
The product does not contain sufficient
technical or engineering documentation (whether on paper or
in electronic form) that contains descriptions of all the
relevant software/hardware elements of the product, such as
its usage, structure, architectural components, interfaces, design, implementation,
configuration, operation, etc.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1068
(Inconsistency Between Implementation and Documented Design)
The implementation of the product is not consistent with the
design as described within the relevant documentation.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1104
(Use of Unmaintained Third Party Components)
The product relies on third-party components that are not
actively supported or maintained by the original developer or a trusted proxy
for the original developer.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1329
(Reliance on Component That is Not Updateable)
The product contains a component that cannot be updated or patched in order to remove vulnerabilities or significant bugs.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1357
(Reliance on Insufficiently Trustworthy Component)
The product is built from multiple separate components, but it uses a component that is not sufficiently trusted to meet expectations for security, reliability, updateability, and maintainability.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1360
(ICS Dependencies (& Architecture)) >
1368
(ICS Dependencies (& Architecture): External Digital Systems) >
1393
(Use of Default Password)
The product uses default passwords for potentially critical functionality.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain)
Weaknesses in this category are related to the "ICS Supply Chain" super category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1369
(ICS Supply Chain: IT/OT Convergence/Expansion)
Weaknesses in this category are related to the "IT/OT Convergence/Expansion" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "The increased penetration of DER devices and smart loads make emerging ICS networks more like IT networks and thus susceptible to vulnerabilities similar to those of IT networks." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1369
(ICS Supply Chain: IT/OT Convergence/Expansion) >
636
(Not Failing Securely ('Failing Open'))
When the product encounters an error condition or failure, its design requires it to fall back to a state that is less secure than other options that are available, such as selecting the weakest encryption algorithm or using the most permissive access control restrictions.
Failing Open

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1369
(ICS Supply Chain: IT/OT Convergence/Expansion) >
284
(Improper Access Control)
The product does not restrict or incorrectly restricts access to a resource from an unauthorized actor.
Authorization

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties)
Weaknesses in this category are related to the "Common Mode Frailties" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "At the component level, most ICS systems are assembled from common parts made by other companies. One or more of these common parts might contain a vulnerability that could result in a wide-spread incident." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
664
(Improper Control of a Resource Through its Lifetime)
The product does not maintain or incorrectly maintains control over a resource throughout its lifetime of creation, use, and release.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
707
(Improper Neutralization)
The product does not ensure or incorrectly ensures that structured messages or data are well-formed and that certain security properties are met before being read from an upstream component or sent to a downstream component.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
710
(Improper Adherence to Coding Standards)
The product does not follow certain coding rules for development, which can lead to resultant weaknesses or increase the severity of the associated vulnerabilities.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
1357
(Reliance on Insufficiently Trustworthy Component)
The product is built from multiple separate components, but it uses a component that is not sufficiently trusted to meet expectations for security, reliability, updateability, and maintainability.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
329
(Generation of Predictable IV with CBC Mode)
The product generates and uses a predictable initialization Vector (IV) with Cipher Block Chaining (CBC) Mode, which causes algorithms to be susceptible to dictionary attacks when they are encrypted under the same key.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1370
(ICS Supply Chain: Common Mode Frailties) >
693
(Protection Mechanism Failure)
The product does not use or incorrectly uses a protection mechanism that provides sufficient defense against directed attacks against the product.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1371
(ICS Supply Chain: Poorly Documented or Undocumented Features)
Weaknesses in this category are related to the "Poorly Documented or Undocumented Features" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Undocumented capabilities and configurations pose a risk by not having a clear understanding of what the device is specifically supposed to do and only do. Therefore possibly opening up the attack surface and vulnerabilities." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1371
(ICS Supply Chain: Poorly Documented or Undocumented Features) >
489
(Active Debug Code)
The product is deployed to unauthorized actors with debugging code still enabled or active, which can create unintended entry points or expose sensitive information.
Leftover debug code

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1371
(ICS Supply Chain: Poorly Documented or Undocumented Features) >
912
(Hidden Functionality)
The product contains functionality that is not documented, not part of the specification, and not accessible through an interface or command sequence that is obvious to the product's users or administrators.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1371
(ICS Supply Chain: Poorly Documented or Undocumented Features) >
1059
(Insufficient Technical Documentation)
The product does not contain sufficient
technical or engineering documentation (whether on paper or
in electronic form) that contains descriptions of all the
relevant software/hardware elements of the product, such as
its usage, structure, architectural components, interfaces, design, implementation,
configuration, operation, etc.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1371
(ICS Supply Chain: Poorly Documented or Undocumented Features) >
1242
(Inclusion of Undocumented Features or Chicken Bits)
The device includes chicken bits or undocumented features that can create entry points for unauthorized actors.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption)
Weaknesses in this category are related to the "OT Counterfeit and Malicious Corruption" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "In ICS, when this procurement process results in a vulnerability or component damage, it can have grid impacts or cause physical harm." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption) >
1278
(Missing Protection Against Hardware Reverse Engineering Using Integrated Circuit (IC) Imaging Techniques)
Information stored in hardware may be recovered by an attacker with the capability to capture and analyze images of the integrated circuit using techniques such as scanning electron microscopy.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption) >
1198
(Privilege Separation and Access Control Issues)
Weaknesses in this category are related to features and mechanisms providing hardware-based isolation and access control (e.g., identity, policy, locking control) of sensitive shared hardware resources such as registers and fuses.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption) >
1231
(Improper Prevention of Lock Bit Modification)
The product uses a trusted lock bit for restricting access to registers, address regions, or other resources, but the product does not prevent the value of the lock bit from being modified after it has been set.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption) >
1233
(Security-Sensitive Hardware Controls with Missing Lock Bit Protection)
The product uses a register lock bit protection mechanism, but it does not ensure that the lock bit prevents modification of system registers or controls that perform changes to important hardware system configuration.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1361
(ICS Supply Chain) >
1372
(ICS Supply Chain: OT Counterfeit and Malicious Corruption) >
284
(Improper Access Control)
The product does not restrict or incorrectly restricts access to a resource from an unauthorized actor.
Authorization

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment))
Weaknesses in this category are related to the "ICS Engineering (Constructions/Deployment)" super category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1373
(ICS Engineering (Construction/Deployment): Trust Model Problems)
Weaknesses in this category are related to the "Trust Model Problems" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Assumptions made about the user during the design or construction phase may result in vulnerabilities after the system is installed if the user operates it using a different security approach or process than what was designed or built." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1373
(ICS Engineering (Construction/Deployment): Trust Model Problems) >
269
(Improper Privilege Management)
The product does not properly assign, modify, track, or check privileges for an actor, creating an unintended sphere of control for that actor.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1373
(ICS Engineering (Construction/Deployment): Trust Model Problems) >
807
(Reliance on Untrusted Inputs in a Security Decision)
The product uses a protection mechanism that relies on the existence or values of an input, but the input can be modified by an untrusted actor in a way that bypasses the protection mechanism.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1373
(ICS Engineering (Construction/Deployment): Trust Model Problems) >
349
(Acceptance of Extraneous Untrusted Data With Trusted Data)
The product, when processing trusted data, accepts any untrusted data that is also included with the trusted data, treating the untrusted data as if it were trusted.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1374
(ICS Engineering (Construction/Deployment): Maker Breaker Blindness)
Weaknesses in this category are related to the "Maker Breaker Blindness" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Lack of awareness of deliberate attack techniques by people (vs failure modes from natural causes like weather or metal fatigue) may lead to insufficient security controls being built into ICS systems." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data)
Weaknesses in this category are related to the "Gaps in Details/Data" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Highly complex systems are often operated by personnel who have years of experience in managing that particular facility or plant. Much of their knowledge is passed along through verbal or hands-on training but may not be fully documented in written practices and procedures." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data) >
1059
(Insufficient Technical Documentation)
The product does not contain sufficient
technical or engineering documentation (whether on paper or
in electronic form) that contains descriptions of all the
relevant software/hardware elements of the product, such as
its usage, structure, architectural components, interfaces, design, implementation,
configuration, operation, etc.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data) >
1110
(Incomplete Design Documentation)
The product's design documentation does not adequately describe
control flow, data flow, system initialization, relationships between tasks,
components, rationales, or other important aspects of the
design.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data) >
710
(Improper Adherence to Coding Standards)
The product does not follow certain coding rules for development, which can lead to resultant weaknesses or increase the severity of the associated vulnerabilities.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data) >
1053
(Missing Documentation for Design)
The product does not have documentation that represents how it is designed.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1375
(ICS Engineering (Construction/Deployment): Gaps in Details/Data) >
1111
(Incomplete I/O Documentation)
The product's documentation does not adequately define inputs,
outputs, or system/software interfaces.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1376
(ICS Engineering (Construction/Deployment): Security Gaps in Commissioning)
Weaknesses in this category are related to the "Security Gaps in Commissioning" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "As a large system is brought online components of the system may remain vulnerable until the entire system is operating and functional and security controls are put in place. This creates a window of opportunity for an adversary during the commissioning process." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1376
(ICS Engineering (Construction/Deployment): Security Gaps in Commissioning) >
276
(Incorrect Default Permissions)
During installation, installed file permissions are set to allow anyone to modify those files.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1376
(ICS Engineering (Construction/Deployment): Security Gaps in Commissioning) >
362
(Concurrent Execution using Shared Resource with Improper Synchronization ('Race Condition'))
The product contains a concurrent code sequence that requires temporary, exclusive access to a shared resource, but a timing window exists in which the shared resource can be modified by another code sequence operating concurrently.
Race Condition

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1376
(ICS Engineering (Construction/Deployment): Security Gaps in Commissioning) >
1393
(Use of Default Password)
The product uses default passwords for potentially critical functionality.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1377
(ICS Engineering (Construction/Deployment): Inherent Predictability in Design)
Weaknesses in this category are related to the "Inherent Predictability in Design" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "The commonality of design (in ICS/SCADA architectures) for energy systems and environments opens up the possibility of scaled compromise by leveraging the inherent predictability in the design." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1362
(ICS Engineering (Constructions/Deployment)) >
1377
(ICS Engineering (Construction/Deployment): Inherent Predictability in Design) >
1278
(Missing Protection Against Hardware Reverse Engineering Using Integrated Circuit (IC) Imaging Techniques)
Information stored in hardware may be recovered by an attacker with the capability to capture and analyze images of the integrated circuit using techniques such as scanning electron microscopy.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance))
Weaknesses in this category are related to the "ICS Operations (& Maintenance)" super category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1378
(ICS Operations (& Maintenance): Gaps in obligations and training)
Weaknesses in this category are related to the "Gaps in obligations and training" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "OT ownership and responsibility for identifying and mitigating vulnerabilities are not clearly defined or communicated within an organization, leaving environments unpatched, exploitable, and with a broader attack surface." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1379
(ICS Operations (& Maintenance): Human factors in ICS environments)
Weaknesses in this category are related to the "Human factors in ICS environments" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Environmental factors in ICS including physical duress, system complexities, and isolation may result in security gaps or inadequacies in the performance of individual duties and responsibilities." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1379
(ICS Operations (& Maintenance): Human factors in ICS environments) >
655
(Insufficient Psychological Acceptability)
The product has a protection mechanism that is too difficult or inconvenient to use, encouraging non-malicious users to disable or bypass the mechanism, whether by accident or on purpose.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1379
(ICS Operations (& Maintenance): Human factors in ICS environments) >
451
(User Interface (UI) Misrepresentation of Critical Information)
The user interface (UI) does not properly represent critical information to the user, allowing the information - or its source - to be obscured or spoofed. This is often a component in phishing attacks.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1380
(ICS Operations (& Maintenance): Post-analysis changes)
Weaknesses in this category are related to the "Post-analysis changes" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Changes made to a previously analyzed and approved ICS environment can introduce new security vulnerabilities (as opposed to safety)." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1381
(ICS Operations (& Maintenance): Exploitable Standard Operational Procedures)
Weaknesses in this category are related to the "Exploitable Standard Operational Procedures" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "Standard ICS Operational Procedures developed for safety and operational functionality in a closed, controlled communications environment can introduce vulnerabilities in a more connected environment." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies)
Weaknesses in this category are related to the "Emerging Energy Technologies" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "With the rapid evolution of the energy system accelerated by the emergence of new technologies such as DERs, electric vehicles, advanced communications (5G+), novel and diverse challenges arise for secure and resilient operation of the system." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
20
(Improper Input Validation)
The product receives input or data, but it does
not validate or incorrectly validates that the input has the
properties that are required to process the data safely and
correctly.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
285
(Improper Authorization)
The product does not perform or incorrectly performs an authorization check when an actor attempts to access a resource or perform an action.
AuthZ

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
295
(Improper Certificate Validation)
The product does not validate, or incorrectly validates, a certificate.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
296
(Improper Following of a Certificate's Chain of Trust)
The product does not follow, or incorrectly follows, the chain of trust for a certificate back to a trusted root certificate, resulting in incorrect trust of any resource that is associated with that certificate.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
346
(Origin Validation Error)
The product does not properly verify that the source of data or communication is valid.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
406
(Insufficient Control of Network Message Volume (Network Amplification))
The product does not sufficiently monitor or control transmitted network traffic volume, so that an actor can cause the product to transmit more traffic than should be allowed for that actor.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1382
(ICS Operations (& Maintenance): Emerging Energy Technologies) >
601
(URL Redirection to Untrusted Site ('Open Redirect'))
The web application accepts a user-controlled input that specifies a link to an external site, and uses that link in a redirect.
Open Redirect
Cross-site Redirect
Cross-domain Redirect
Unvalidated Redirect

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1383
(ICS Operations (& Maintenance): Compliance/Conformance with Regulatory Requirements)
Weaknesses in this category are related to the "Compliance/Conformance with Regulatory Requirements" category from the SEI ETF "Categories of Security Vulnerabilities in ICS" as published in March 2022: "The ICS environment faces overlapping regulatory regimes and authorities with multiple focus areas (e.g., operational resiliency, physical safety, interoperability, and security) which can result in cyber security vulnerabilities when implemented as written due to gaps in considerations, outdatedness, or conflicting requirements." Note: members of this category include "Nearest IT Neighbor" recommendations from the report, as well as suggestions by the CWE team. These relationships are likely to change in future CWE versions.

1358
(Weaknesses in SEI ETF Categories of Security Vulnerabilities in ICS) >
1363
(ICS Operations (& Maintenance)) >
1383
(ICS Operations (& Maintenance): Compliance/Conformance with Regulatory Requirements) >
710
(Improper Adherence to Coding Standards)
The product does not follow certain coding rules for development, which can lead to resultant weaknesses or increase the severity of the associated vulnerabilities.
Relationship
Relationships in this view are not authoritative and subject to change. See Maintenance notes.
Maintenance
This view was created in CWE 4.7 to facilitate and illuminate discussion about weaknesses in ICS with [REF-1248] as a starting point. After the release of CWE 4.9 in October 2022, this has been under active review by members of the "Boosting CWE" subgroup of the CWE-CAPEC ICS/OT Special Interest Group (SIG). Relationships are still subject to change. In addition, there may be some issues in [REF-1248] that are outside of the current scope of CWE, which will require consultation with many CWE stakeholders to resolve.
More information is available — Please edit the custom filter or select a different filter. |
|
Use of the Common Weakness Enumeration (CWE™) and the associated references from this website are subject to the Terms of Use. CWE is sponsored by the U.S. Department of Homeland Security (DHS) Cybersecurity and Infrastructure Security Agency (CISA) and managed by the Homeland Security Systems Engineering and Development Institute (HSSEDI) which is operated by The MITRE Corporation (MITRE). Copyright © 2006–2024, The MITRE Corporation. CWE, CWSS, CWRAF, and the CWE logo are trademarks of The MITRE Corporation. |
||